In this article as we explore the seamless process of transferring FSMO roles to another Domain Controller, leveraging the power of PowerShell. This guide will walk you through two distinct approaches – one involving a single command to move all roles simultaneously, and the other requiring individual commands for moving each role. Whether you prefer a consolidated or a more granular approach, this article provides step-by-step procedures for both methods, ensuring a smooth transition of Flexible Single Master Operations roles within your Active Directory environment.
The decision to transfer FSMO roles may arise in various scenarios, including:
- Demotion of a Domain Controller:
- When retiring or decommissioning a Domain Controller.
- Change in IP Addresses:
- If there is a need to modify the IP addresses associated with a Domain Controller.
- Domain Controller Maintenance:
- Temporarily taking a Domain Controller offline for maintenance or troubleshooting.
- Operating System Upgrade:
- When upgrading the Operating System of a Domain Controller.
- Addressing Performance Issues:
- To resolve or optimize performance-related issues within the domain.
- Hardware Upgrade or Replacement:
- When upgrading the hardware or replacing the existing hardware of a Domain Controller.
- Site or Location Changes:
- If there are changes in the physical location or site of a Domain Controller.
- Disaster Recovery:
- As part of a disaster recovery strategy, especially when restoring a Domain Controller from backup.
- Security Concerns:
- In response to security vulnerabilities or concerns, transferring FSMO roles can be part of a security protocol.
- Consolidation or Redistribution:
- When consolidating or redistributing roles across Domain Controllers for better organizational or operational efficiency.
- Domain Restructuring:
- During significant changes in the domain structure, such as mergers, acquisitions, or organizational restructuring.
- Software Updates and Patching:
- In cases where software updates or patching necessitate a temporary transfer of roles.
Considering these factors will help administrators make informed decisions when managing FSMO roles in a dynamic and evolving domain environment.
In a previous article, we learned How To Find FSMO Roles Holders In Active Directory
The below two commands are part from the above article.
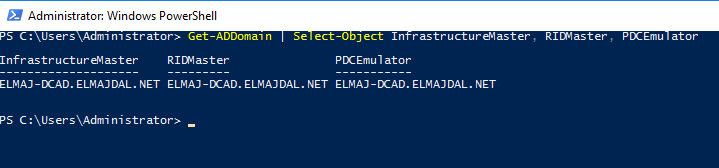
Execute the Get-ADDomain cmdlet to retrieve information about the RID master, PDC emulator, and Infrastructure master roles.
- Get-ADDomain | Select-Object InfrastructureMaster, RIDMaster, PDCEmulator

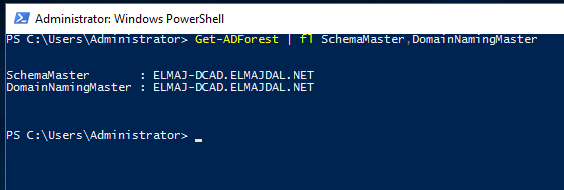
Execute the Get-ADForest cmdlet to obtain details about the Schema master and Domain naming master roles.
- Get-ADForest | fl SchemaMaster,DomainNamingMaster

Now that we know the Domain Controller(s) that holds the FSMO roles, we are ready to transfer the roles to a different Domain Controller(s). For example in my case, the domain controller that is holding the FSMO roles is named : ELMAJ-DCAD
We can transfer the roles all together with a single command to a new domain controller, or if you want to transfer the roles to different domain controllers, you have a command to transfer each role separately. In the below section, I will be showing these commands.
Choice 1: Perform the transfer of ALL FSMO roles using a single PowerShell command
To execute the following command without encountering errors, ensure that your account is part of the Schema Admins group. If it isn’t, an error will occur. Once the account has been added to the Schema Admins group, you need to sign off and then sign back in for the changes to take effect.
- Move-ADDirectoryServerOperationMasterRole “NewDCNameHere” -OperationMasterRole PDCEmulator,RIDMaster,InfrastructureMaster,SchemaMaster,DomainNamingMaster -Confirm:$false
Where NewDCNameHere is the new Domain Controller you want to move the Roles to it. Replace this with your desired domain controller name.
Notes
- Replace NewDCNameHere with your desired domain controller name.
- For Schema master role: Ensure that your account is part of the Schema Admins group. If it isn’t, an error will occur. Once the account has been added to the Schema Admins group, you need to sign off and then sign back in for the changes to take effect.